RANSOMWARE - BEWARE!
WHAT IS IT?
Just recently (September 2023), ransomware cyber-attacks crippled a number of casinos and hotels in Las Vegas owned by Caesers Entertainment and MGM Resorts International. Unfortunately, cyber-attacks, especially ransomware, can happen to anyone, anywhere. Here is some information...
Ransomware, a malicious software or malware, is a technique used by hackers (cybercriminals) to encrypt documents on a PC, lock out the user, and demand a ransom to regain access to the data on the computer.
This type of malware can typically enter a PC either through an email attachment or directly from a browser, if a website infected with it is visited. It is also able to access a PC data through a network.
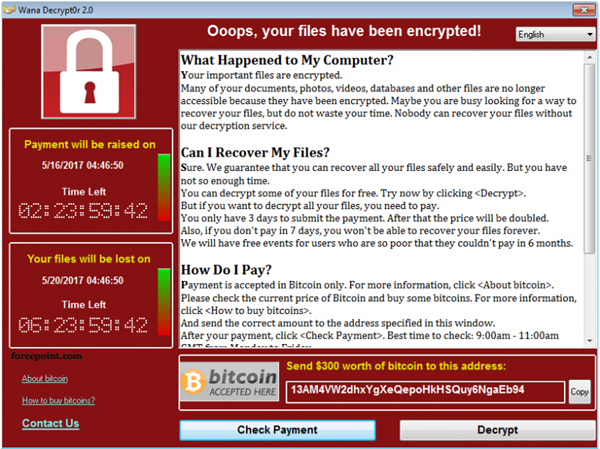
In recent years, extremely malicious ransomware attacks were caused by malware such as WannaCry (WanaCrypt0r 2.0, or WCry) and NotPetya. WannaCry was a type of ransomworm, a piece of malware that can self-replicate, and continue to grow exponentially, just as a real disease does.
NotPetya was different in that it didn’t seem it was created to make money as other ransomware does. Even if users did pay, their data could never be recovered. NotPetya seemed to be a deliberate, malicious, and destructive attack.
These two wreaked havoc across the globe in 2017. They sparked so much alarm that more people than ever before had good reason to back up their files. Backing up files effectively deadens a ransomware attack. Even so, too many of us have short memories and cybersecurity experts warn against getting lazy about backing up files.
RANSOMWARE HISTORY
c
ENCRYPTION and RANSOMWARE
Encryption is the innovation that enabled ransomware authors to not only lock up the screen but encrypt all the data. This meant the data would still be locked up even if the user was able to uninstall the ransomware itself. The user had to make the payment in order to get the unlock key.
Cryptolocker, was an example of a piece of ‘cryptoransomware’ found active in 2013 and 2014. Petya has been active since 2016. Other examples of this type of ransomware include Cerby and Locky, among others.
Ever since the first attack, it has been a relentless duel of one-upmanship between the bad guys and the cybersecurity experts and researchers. Unfortunately, ransomware is still alive and well.
BITCOINS and RANSOMWARE
The early types of malware did not last long because bank transfers could be tracked and cash payments were hard to pull off. It was the invention of the bitcoin in 2009 that gave the hackers the means to take ransom payment without involving banks.
MOBILE PHONES and RANSOMWARE
Ransomware can also attack and lock users out of their Android mobile phones. The open-source nature of the Android operating system makes Android phones more vulnerable to attack. One malware was actually able to avoid detection from Google’s security system and was downloaded in an app from the Google Play Store.
Google cannot control all Android mobile phones, only its own phones, the Nexus and Pixel phones, whereas iPhones are less vulnerable because Apple can push security updates quickly to all its phones at once.
WHO DOES RANSOMWARE ATTACK?
Although many cybercriminals target specific institutions and organizations, the reality is most ransomware attacks are made at random. The criminals will go after anyone with a computer.
HOW TO PROTECT YOURSELF FROM RANSOMWARE...
WHAT TO DO...
- Back up your files off the network. Then back up and back up some more. A comprehensive backup strategy can help blunt the force of a ransomware attack. A person’s information cannot be held hostage when it is stored securely off network. All too many people believe they won’t be attacked until they are. If and when this occurs, it’s crucial to have all your data backed up and stored in a safe, secure place.
- Use devices not connected to the network to backup.
- Use different media types.
- Keep a copy off-site.
- Encrypt your sensitive backups. There are several pieces of encryption software available today.
- If backing up to a cloud, choose one with threat-protection features. Many ransomware variants can infect any attached drives or network files that are accessible, including those that are cloud-based.
- Disk cloning and disk imaging are other ways to keep your files safe. Cloning and imaging software programs are available.
- Make sure your passwords are strong and unique.
- Be sure a reputable company has produced your antivirus software. There is a lot of fake software out there.
- Maintain a secure firewall and keep your security software up to date. It defends your PC 24/7 on the Internet while keeping pace with the latest malware threats. Always remember the cybercriminals know more about the flaws in your PC’s protection than you ever will, and constant patching with updates corrects those flaws.
- Use content scanning and filtering on your mail servers. Inbound emails should be scanned for known threats and block attachment types that could pose a treat.
WHAT NOT TO DO...
- Do NOT click on any links and attachments to unexpected and unknown emails. Be especially wary of Microsoft Office attachments requesting that you enable macros to view the content. Immediately delete any email saying a package awaits you that could not be delivered, or there is a terrific screensaver you should install.
- Do NOT pay any ransom. Although paying may seem like a realistic response, there is no guarantee you'll ever regain access to your files. Not only does your payment fund and encourage your attackers, but they can also charge you time and again to recover your stolen data.
- Turn off your computer after it's been infected. Doing so may remove not only vital details of the attack but also files required to turn on your computer again, as well as opportunities to disinfect and restore it to health.
- If the virus has infected your back-ups, contact a professional recovery service in an attempt to recover data or work around the ransomware to regain it.
- Before you restore your files from a backup, first clean and update your computer.
THE IMPORTANCE OF BACKING UP
March 31st is designated as globally recognized World Backup Day. It is a day used as a reminder of how and why complete, regular backups deserve a place on the to-do list. March 31st was chosen to remind people to back up or risk losing data and becoming an April Fool!
World Backup Day also includes offers and special deals from many hardware and software companies to mark the date.
PLEASE NOTE: If the information provided in this article is above your level of computer understanding, please contact a reputable IT person or company for suggestions.
"The Cleanest Clean You've Ever Seen."
by
ABC Oriental Rug & Carpet Cleaning Co.
130 Cecil Malone Drive Ithaca, NY 14850
607-272-1566

ABC
Carpet & Rug
Spotting Guide

ABC Oriental Rug & Carpet Cleaning Co.
is a FOUNDING MEMBER of the
Association
of Rug Care Specialists.
"To Teach, Cultivate and Advance the Art and Science
of Rug Care"
ABC
Carpet & Rug
Spotting Guide
Learn how to remove spots with ordinary household solutions
Sign up below to gain access to your complementary Spotting Guide from ABC.
Registering your email address guarantees you will be notified whenever discount savings coupons become available.
Did you know that our ABC Responsible Care Spotter can get those pesky spots out of your carpet and rugs and will work equally as well on your clothes and upholstery?
Stop by our office and pick one up. They are $5.00 + Tax but if you have carpets or upholstery cleaned in your home or business, just request a free one from your Technician.
And don't forget to fill out the form above to download your free ABC Spotting Guide!